
The Cisco 350-701 SCOR (Implementing and Operating Cisco Security Core Technologies) is one of the core exams in the Cisco security framework. This exam is not only an essential pathway to obtaining CCNP Security and CCIE Security certifications but also a benchmark for assessing your capabilities in core network security domains.
The exam code is 350-701 SCOR, with a duration of 120 minutes, containing approximately 90–110 questions, and a passing score of around 80%. The exam primarily evaluates candidates’ comprehensive abilities in areas such as security architecture design, access control, threat protection, VPN technologies, and network security automation.
In the current era of accelerating digital transformation in enterprises, the demand for network security positions is growing exponentially. Passing the SCOR exam not only demonstrates your proficiency in operating Cisco security core technologies but also lays a solid foundation for advancing to CCIE Security.
Table of Contents
- Why 350-701 SCOR is a Key Stepping Stone in a Network Security Career
- Structure and Core Content of the Cisco SCOR Exam
- Differences Between CCIE Security and CCNP Security
- How to Efficiently Prepare Using 350-701 Dumps
- Leads4Pass: A Reliable Source for Exam Materials
- Key Strategies for Passing the Cisco 350-701 SCOR Exam
- Salary and Career Development Trends After Passing the SCOR 350-701 Exam
- Sharing the Latest 350-701 SCOR Exam Questions
- How to Maintain the Long-Term Value of Certifications
- Conclusion: Make 350-701 Your Stepping Stone in a Security Career
Why 350-701 SCOR is a Key Stepping Stone in a Network Security Career
Whether you are a newcomer just entering the network security field or a mid-level security engineer aspiring to advance to a security architect role, 350-701 serves as a pivotal watershed in your professional development. Cisco certifications are regarded globally as the “gold standard” in the IT industry, particularly in enterprise-level network security.
Through 350-701, you will master the industry’s most core security technology stack, including:
- Network Security Architecture Design: Learn how to build end-to-end defense systems;
- Zero Trust Access Control: Gain in-depth understanding of identity security and access policies;
- VPN and Secure Encrypted Communications: Cover key technologies such as IPSec, SSL, and DMVPN;
- Security Automation: Implement automated defenses using Python, REST APIs, and Cisco DNA Center.
More importantly, many enterprises list CCNP or CCIE Security as “preferred qualifications” when recruiting for security positions. This means that passing this exam will make your resume significantly more competitive.
Cisco SCOR Exam Structure and Core Content
The Cisco 350-701 SCOR exam content covers five major domains of Cisco Security Core Technologies, each occupying different weight percentages:
| Module | Main Content | Weight |
|---|---|---|
| Security Network Architecture | Security Design, Segmentation, Network Access Control | 20% |
| Secure Cloud and Content Security | Cloud Security Policies, DNS Protection, Web Filtering | 15% |
| Network Threat Detection and Protection | Firewalls, IPS, Malware Analysis | 25% |
| Secure Endpoint and Access | VPN, AAA, ISE, Remote Access | 20% |
| Automation and Programmability | Python, REST API, Cisco DNA Center | 20% |
This is not merely a theoretical exam; it also evaluates whether candidates can apply Cisco’s security tools in real-world scenarios. For example, how to deploy Cisco Firepower Threat Defense (FTD), how to use ISE for access control, and how to implement cloud security protection through Cisco Umbrella.
Differences Between CCIE Security and CCNP Security
Although both belong to Cisco’s security certification framework, their positioning and difficulty levels are completely different.
- CCNP Security represents mid-to-senior security engineers, primarily focusing on security device configuration and operations;
- CCIE Security, on the other hand, is an expert-level certification that emphasizes network security architecture design, policy implementation in complex environments, and troubleshooting capabilities.
To obtain CCIE Security certification, one must first pass the 350-701 SCOR exam, followed by the CCIE Security Lab Exam. Therefore, 350-701 serves as the starting point for all security experts.
For professionals aspiring to join international security teams or multinational enterprises, the differences between CCNP and CCIE extend beyond skill depth to salary and career influence. According to Global Knowledge data, CCIE certification holders earn an average annual salary approximately 27% higher than CCNP holders.
How to Efficiently Prepare for the Exam Using 350-701 Dumps
Among numerous study materials, 350-701 Dumps is one of the most practical preparation tools. It helps candidates quickly understand the exam question types, master key points and difficulties, and reinforce memory through simulations of real questions.
One recommended source is Leads4Pass (https://www.leads4pass.com/350-701.html), which provides PDF and VCE versions containing 784 latest questions and answers, covering all knowledge points in the Cisco official syllabus, and regularly updated as of October 15, 2025.
However, using Dumps cannot replace systematic learning. The best preparation strategy is:
- First, study the official course content (such as Implementing and Operating Cisco Security Core Technologies v1.1 provided by Cisco Learning Partners);
- Combine 350-701 Dumps to test the depth of understanding;
- Identify and fill gaps through 350-701 VCE mock exams;
- Hands-on configuration practice: Set up environments in EVE-NG, GNS3, or Cisco Packet Tracer to perform drills.
This learning approach that combines theory and practice ensures that you can handle both the exam and actual work with ease.
Leads4Pass: A Reliable Source for Exam Materials
Leads4Pass is widely recommended because the Cisco certification exam materials it provides maintain industry-leading accuracy and update speed. The platform’s 350-701 SCOR Dumps not only include detailed question explanations but also feature a simulation exam environment (VCE mode), allowing candidates to test their knowledge mastery in realistic scenarios.
More importantly, Leads4Pass’s question bank content is compiled based on official exam objectives (Exam Objectives), with coverage exceeding 95%. This means that by systematically studying and practicing these questions, candidates can significantly improve their pass rates. Statistics show that candidates using Leads4Pass question banks achieve an average pass rate of up to 99.5%, far higher than the average level for learners not using question banks.
In addition, Leads4Pass provides users with:
- PDF format for convenient offline review;
- VCE format for interactive simulation exams;
- Regular update notifications (checked 1-2 times per month, with full updates within 3 working days if official changes occur);
- Free exam dumps updates for one year after purchase (365 days policy).
Therefore, if you are preparing for CCNP or CCIE Security, Leads4Pass’s 350-701 Dumps is undoubtedly a trustworthy learning resource.
Key Strategies for Passing the Cisco 350-701 SCOR Exam
The 350-701 SCOR exam covers a broad range of content and diverse question types. To pass it smoothly, you must develop a clear study plan and efficient preparation strategies. Below are three core methods for successfully passing the exam:
① Develop a Phased Learning Plan
Divide Cisco Security Core Technologies into five major modules, focusing on one module per week. For example:
- Week 1: Study network security architecture;
- Week 2: Research access control and identity management;
- Week 3: Dive deep into firewalls and intrusion prevention systems;
- Week 4: Focus on automation and programmable security.
This “modular learning” approach makes the knowledge system clearer and reduces confusion.
② Emphasize Hands-On Training in Lab Environments
The essence of Cisco certification exams lies in “doing rather than just knowing.” It is recommended to use Cisco VIRL, EVE-NG, or GNS3 to create virtual lab environments and practice core technologies such as firewall policy configuration, VPN tunnel establishment, and Cisco ISE authentication. These skills not only help you tackle scenario-based questions on the exam but can also be directly applied in the workplace.
③ Simulate Exams and Analyze Errors
Conducting simulated exams to assess learning outcomes is extremely important. It is advised to perform a mock test of about 50 questions after completing each chapter. For incorrect questions, deeply analyze whether the issue stems from conceptual ambiguity or configuration details, record them, and review them repeatedly. This “error reflection method” can significantly improve answer accuracy.
Salary and Career Development Trends After Passing the SCOR 350-701 Exam
Network security positions are currently in a phase of extreme global supply-demand imbalance. According to the (ISC)² 2025 report, there are still over 3.5 million cybersecurity job vacancies worldwide. Among them, the demand for Cisco Security professionals ranks in the top five.
In the North American region, engineers with CCNP Security certification have an average annual salary of $118,000, while experts with CCIE Security can reach $156,000 or more. In the Asia-Pacific region (including mainland China, Hong Kong, and Singapore), certified engineers’ salaries are generally 20% or more higher than those without certification.
The typical career development path is as follows:
| Position | Experience Required | Average Annual Salary |
|---|---|---|
| Junior Network Security Engineer | 0–2 years | $65,000 |
| CCNP Security Engineer | 2–5 years | $100,000 |
| Security Architect | 5–8 years | $130,000 |
| CCIE Security Expert | 8+ years | $156,000+ |
It is evident that the 350-701 SCOR is not just an exam; it is your passport to entering the high-salary security field.
Latest 350-701 SCOR Exam Question Sharing
Here are a few free sample questions based on the latest 350-701 exam objectives. These examples reflect the difficulty and style of the real exam:
| Number of exam questions | From | Release time |
| 15 (Free) | Leads4pass | Oct 24, 2025 |
Question 1:
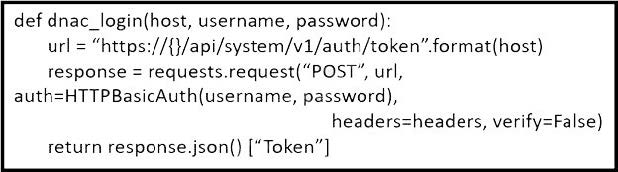
Refer to the exhibit. What is the result of the Python script?
A. It uses the POST HTTP method to obtain a username and password to be used for authentication.
B. It uses the POST HTTP method to obtain a token to be used for authentication.
C. It uses the GET HTTP method to obtain a token to be used for authentication.
D. It uses the GET HTTP method to obtain a username and password to be used for authentication
Correct Answer: B
Question 2:
What are two reasons for implementing a multifactor authentication solution such as Duo Security provide to an organization? (Choose two)
A. flexibility of different methods of 2FA such as phone callbacks, SMS passcodes, and push notifications
B. single sign-on access to on-premises and cloud applications
C. integration with 802.1x security using native Microsoft Windows supplicant
D. secure access to on-premises and cloud applications
E. identification and correction of application vulnerabilities before allowing access to resources
Correct Answer: AD
Explanation:
Two-factor authentication adds a second layer of security to your online accounts. Verifying your identity using asecond factor (like your phone or other mobile device) prevents anyone but you from logging in, even if theyknow your password.
Note: Single sign-on (SSO) is a property of identity and access management that enables users to securelyauthenticate with multiple applications and websites by logging in only once with just one set of credentials(username and password). With SSO, the application or website that the user is trying to access relies on atrusted third party to verify that users are who they say they are.
Question 3:
What are two functions of secret key cryptography? (Choose two)
A. key selection without integer factorization
B. utilization of different keys for encryption and decryption
C. utilization of large prime number iterations
D. provides the capability to only know the key on one side
E. utilization of less memory
Correct Answer: AE
Question 4:
Which technology limits communication between nodes on the same network segment to individual applications?
A. serverless infrastructure
B. microsegmentation
C. SaaS deployment
D. machine-to-machine firewalling
Correct Answer: B
Question 5:
A university policy must allow open access to resources on the Internet for research, but internal workstations are exposed to malware. Which Cisco AMP feature allows the engineering team to determine whether a file is installed on a selected few workstations?
A. file prevalence
B. file discovery
C. file conviction
D. file manager
Correct Answer: A
Question 6:
When configuring ISAKMP for IKEv1 Phase1 on a Cisco IOS router, an administrator needs to input the command crypto isakmp key cisco address 0.0.0.0. The administrator is not sure what the IP addressing in this command issued for. What would be the effect of changing the IP address from 0.0.0.0 to 1.2.3.4?
A. The key server that is managing the keys for the connection will be at 1.2.3.4
B. The remote connection will only be allowed from 1.2.3.4
C. The address that will be used as the crypto validation authority
D. All IP addresses other than 1.2.3.4 will be allowed
Correct Answer: B
Explanation:
The command crypto isakmp key cisco address 1.2.3.4 authenticates the IP address of the 1.2.3.4 peer by using the key cisco. The address of “0.0.0.0” will authenticate any address with this key
Question 7:
A security test performed on one of the applications shows that user input is not validated. Which security vulnerability is the application more susceptible to because of this lack of validation?
A. denial -of-service
B. cross-site request forgery
C. man-in-the-middle
D. SQL injection
Correct Answer: D
Explanation:
An application that does not validate user input is particularly susceptible to SQL injection attacks. In an SQL injection attack, an attacker can insert or “inject” a SQL query via the input data from the client to the application. Due to the lack of validation, the malicious SQL commands are executed by the database server, leading to unauthorized access or manipulation of the database.
Question 8:
Which two aspects of the IaaS cloud service model are managed by the service provider? (Choose two.)
A. virtual machines
B. physical network
C. applications
D. hypervisors
E. virtual network
Correct Answer: BD
Question 9:
How does Cisco AMP for Endpoints provide next-generation protection?
A. It encrypts data on user endpoints to protect against ransomware.
B. It leverages an endpoint protection platform and endpoint detection and response.
C. It utilizes Cisco pxGrid, which allows Cisco AMP to pull threat feeds from threat intelligence centers.
D. It integrates with Cisco FTD devices.
Correct Answer: B
Question 10:
Which two are valid suppression types on a Cisco Next Generation Intrusion Prevention System? (Choose two)
A. Port
B. Rule
C. Source
D. Application
E. Protocol
Correct Answer: BC
Question 11:
What is the term for when an endpoint is associated to a provisioning WLAN that is shared with guest access, and the same guest portal is used as the BYOD portal?
A. single-SSID BYOD
B. multichannel GUI
C. dual-SSID BYOD
D. streamlined access
Correct Answer: C
Question 12:
In which two ways does a system administrator send web traffic transparently to the Web Security Appliance? (Choose two)
A. configure Active Directory Group Policies to push proxy settings
B. configure policy-based routing on the network infrastructure
C. reference a Proxy Auto Config file
D. configure the proxy IP address in the web-browser settings
E. use Web Cache Communication Protocol
Correct Answer: BE
Question 13:
What are two workloaded security models? (Choose two)
A. SaaS
B. IaaS
C. on-premises
D. off-premises
E. PaaS
Correct Answer: CD
Question 14:
What is a functional difference between Cisco AMP for Endpoints and Cisco Umbrella Roaming Client?
A. The Umbrella Roaming client stops and tracks malicious activity on hosts, and AMP for Endpoints tracks only URL-based threats.
B. The Umbrella Roaming Client authenticates users and provides segmentation, and AMP for Endpoints allows only for VPN connectivity
C. AMP for Endpoints authenticates users and provides segmentation, and the Umbrella Roaming Client allows only for VPN connectivity.
D. AMP for Endpoints stops and tracks malicious activity on hosts, and the Umbrella Roaming Client tracks only URL-based threats.
Correct Answer: B
Question 15:
Refer to the exhibit.
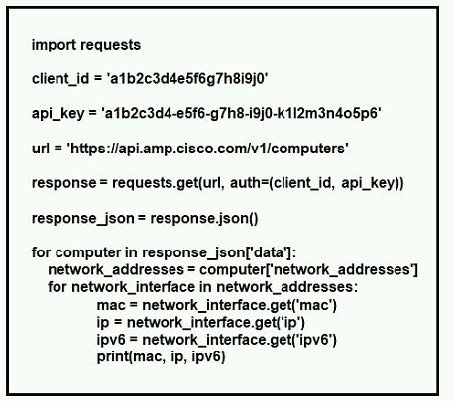
What does the API do when connected to a Cisco security appliance?
A. get the process and PID information from the computers in the network
B. create an SNMP pull mechanism for managing AMP
C. gather network telemetry information from AMP for endpoints
D. gather the network interface information about the computers AMP sees
Correct Answer: D
…
How to Maintain the Long-Term Value of Certifications
Cisco certifications typically have a validity period of three years, meaning you need to continuously learn and update your knowledge to maintain their validity. But more importantly, the core of staying professionally competitive lies in continuous learning.
Here are three recommendations for maintaining the long-term value of certifications:
① Regularly Update Skills and Certifications Cisco officially provides the Continuing Education (CE) program, through which you can earn CE credits by taking courses, participating in projects, or retaking exams to renew your certification. For example, completing 80 CE hours can renew CCNP Security certification.
② Focus on Technology Trends: Security Automation and Zero Trust Architecture In the next 3–5 years, network security will revolve around automated responses, threat intelligence integration, and zero trust security models. By learning emerging technologies such as Cisco SecureX and Cisco XDR, you can stay synchronized with the industry. [Source: Gartner 2025 Security Trends Report]
③ Practice Over Theory Participate in enterprise security projects, SOC operations, or cloud security migration projects to accumulate practical experience. These hands-on experiences will form a strong advantage on your professional resume and give you deeper competitiveness beyond certifications.
Make 350-701 Your Stepping Stone in a Security Career
The Cisco 350-701 SCOR is not just a certification exam; it is a crucial starting point in your network security career. It opens doors to high-salary, secure, and international job opportunities, while also laying a solid foundation for future challenges like CCIE Security.
From a skills perspective, SCOR covers the most core security modules: network architecture, security defense, identity management, and automated protection. Through this certification, you gain not only technical recognition but also the trust of employers on a professional level.
If you aspire to join the security teams of global top-tier enterprises or become a senior expert capable of independently designing security architectures, now is the perfect time to start preparing for the 350-701 SCOR.
Common Questions (FAQs)
- What language versions are available for the 350-701 SCOR exam?
The exam currently supports English and Japanese, and can be scheduled at Pearson VUE test centers worldwide. - After passing 350-701, can I directly take the CCIE exam?
Yes, SCOR is a prerequisite for the CCIE Security lab exam. After passing SCOR, you qualify to challenge the expert-level certification. - Is the pass rate for Cisco SCOR high?
According to industry data, the pass rate is approximately 70–75%. If combined with official courses and 350-701 Dumps simulation training (https://www.leads4pass.com/350-701.html), the pass rate can be increased to 90%. - How should I continue to improve after obtaining CCNP Security?
You can choose to advance to CCIE Security, learn Cisco DevNet automation courses, or expand into cloud security fields (such as AWS/Azure Security certifications).