CCIE Security/CCNP Security 350-701 Dumps is the Cisco 350-701 SCOR exam material for launching your career in cybersecurity operations.
leads4pass 350-701 Dumps Prepares Candidates for Cisco SCOR Exam Questions and Answers
https://www.leads4pass.com/350-701.html helps you earn the Cisco CCIE Security/CCNP Security Exam Certification.
Cisco technology is spread all over the world. This means that CCIE Security/CCNP Security certified professionals will continue to be sought after, as long as you ensure that you can successfully achieve the CCIE Security/CCNP Security 350-701 certification. Use the CCIE Security/CCNP Security 350-701 dumps to guarantee your success with the Cisco CCNP Security Core exam certification.
CCIE Security/CCNP Security Core exam FAQs: About, Benefits, Exam Material
About 350-701 SCOR: What You Need to Know
Vendor: Cisco
Exam Code: 350-701
Exam Name: Implementing and Operating Cisco Security Core Technologies (SCOR)
Certification: CCNP Security
Languages: English and Japanese
Price: $400 USD
Duration: 120 mins
Number of Questions: 90-110 questions
Passing score: 80% Approx
350-701 dumps (PDF and VCE): https://www.leads4pass.com/350-701.html (CCIE Security/CCNP Security core exam dumps maps to Cisco 350-701 SCOR exam objectives)
350-701 dumps (Number of Questions): 542 Q&A
Last update time: Sep 30, 2022
Benefits of passing the 350-701 SCOR exam
Your entry point for obtaining the CCIE Security/CCNP security core certification is the CCNP 350-701 SCOR. Several advantages will come your way if you wear the CCNP badge, including:
1. Have an attractive resume
You can find out all of the details about your training, expertise, and qualifications on your CV. Employers will be drawn to you because of the CCNP badge on your resume and will want you to join their team. Most likely, the company will recognize that you are the greatest and hire you right away.
2. Boost your confidence
You will be considered a Cisco Certified Expert-Security Core after completing the 350-701 test, and you will be qualified to sit for the CCNP or CCIE Security certification exams. You can apply for jobs and take on roles connected to your field with confidence after passing the test. Despite not having a college degree, you can gain confidence because you have established yourself as one of the most informed and experienced specialists in a field that is expanding quickly.
3. High salary
We are all aware that an IT expert with a Cisco certification makes more money than an uncertified counterpart. You can obtain the CCIE security expert qualification by passing the 350-701 SCOR exam, which will open up many fantastic, well-paying career options for you. The income of CCNP security badge holders with certifications is 20% to 25% greater than that of coworkers without certifications.
Free share of a portion of the CCNP Security 350-701 SCOR exam material
| Number of exam questions | Exam name | From | Release time |
| 13 | Implementing and Operating Cisco Security Core Technologies (SCOR) | leads4pass | Oct 08, 2022 |
NEW QUESTION 1:
On which part of the IT environment does DevSecOps focus?
A. application development
B. wireless network
C. data center
D. perimeter network
Correct Answer: A
NEW QUESTION 2:
An organization wants to implement a cloud-delivered and SaaS-based solution to provide visibility and threat detection across the AWS network. The solution must be deployed without software agents and rely on AWS VPC flow logs instead.
Which solution meets these requirements?
A. NetFlow collectors
B. Cisco Cloudlock
C. Cisco Stealthwatch Cloud
D. Cisco Umbrella
Correct Answer: C
Reference: https://www.cisco.com/c/en/us/products/security/stealthwatch-cloud/index.html
NEW QUESTION 3:
A company is experiencing exfiltration of credit card numbers that are not being stored on-premise. The company needs to be able to protect sensitive data throughout the full environment.
Which tool should be used to accomplish this goal?
A. Security Manager
B. Cloudlock
C. Web Security Appliance
D. Cisco ISE
Correct Answer: B
Cisco Cloudlock is a cloud-native cloud access security broker (CASB) that helps you move to the cloud safely. It protects your cloud users, data, and apps.
Cisco Cloudlock provides visibility and compliance checks, protects data against misuse and exfiltration, and provides threat protections against malware like ransomware.
NEW QUESTION 4:
Which security product enables administrators to deploy Kubernetes clusters in air-gapped sites without needing Internet access?
A. Cisco Container Platform
B. Cisco Content Platform
C. Cisco Cloud Platform
D. Cisco Container Controller
Correct Answer: A
NEW QUESTION 5:
Why should organizations migrate to an MFA strategy for authentication?
A. Single methods of authentication can be compromised more easily than MFA.
B. Biometrics authentication leads to the need for MFA due to its ability to be hacked easily.
C. MFA methods of authentication are never compromised.
D. MFA does not require any piece of evidence for an authentication mechanism.
Correct Answer: A
NEW QUESTION 6:
A company discovered an attack propagating through its network via a file. A custom file policy was created in order to track this in the future and ensure no other endpoints execute the infected file.
In addition, it was discovered during testing that the scans are not detecting the file as an indicator of compromise.
What must be done in order to ensure that the created is functioning as it should?
A. Create an IP block list for the website from which the file was downloaded
B. Block the application that the file was used to open
C. Upload the hash for the file into the policy
D. Send the file to Cisco Threat Grid for dynamic analysis
Correct Answer: C
NEW QUESTION 7:
What are the two functionalities of northbound and southbound APIs within Cisco SDN architecture? (Choose two.)
A. Southbound APIs utilize CLI, SNMP, and RESTCONF.
B. Southbound interfaces utilize device configurations such as VLANs and IP addresses.
C. Northbound APIs utilize RESTful API methods such as GET, POST, and DELETE.
D. Southbound APIs are used to define how SDN controllers integrate with applications.
E. Northbound interfaces utilize OpenFlow and OpFlex to integrate with network devices.
Correct Answer: AC
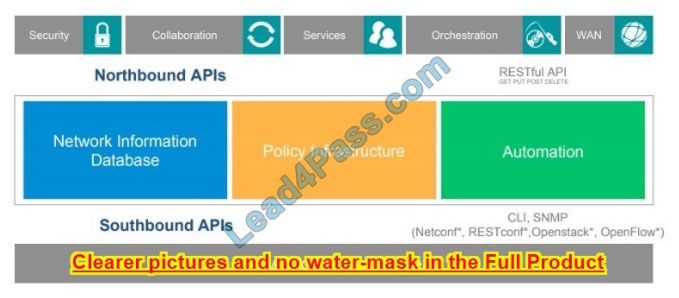
NEW QUESTION 8:
A malicious user gained network access by spoofing printer connections that were authorized using MAB on four different switch ports at the same time.
What two catalyst switch security features will prevent further violations? (Choose two)
A. DHCP Snooping
B. 802.1AE MacSec
C. Port security
D. IP Device track
E. Dynamic ARP inspection
F. Private VLANs
Correct Answer: AE
NEW QUESTION 9:

Refer to the exhibit. All servers are in the same VLAN/Subnet DNS Server-1 and DNS Server-2 must communicate with each other and all servers must communicate with the default gateway multilayer switch.
Which types of private VLAN ports should be configured to prevent communication between DNS servers and the file server?
A. Configure GigabitEthemet0/1 as community port, GigabitEthernet0/2 as promiscuous port GigabitEthernet0/3 and GigabitEthernet0/4 as isolated ports
B. Configure GigabitEthernet0/1 as a promiscuous port, GigabitEthernet0/2 as an isolated port, and GigabitEthernet0/3 and GigabitEthernet0/4 as community ports
C. Configure GigabitEthernet0/1 as a promiscuous port, GigabitEthernet0/2 as a community port, and GigabitEthernet0/3 and Gigabit Ethernet0/4 as isolated ports
D. Configure GigabitEthernet0/1 as a community port GigabitEthernet0/2 as an isolated port, and GigabitEthernet0/3 and GigabitEthernet0/4 as promiscuous ports
Correct Answer: B
NEW QUESTION 10:
In which type of attack does the attacker insert their machine between two hosts that are communicating with each other?
A. LDAP injection
B. man-in-the-middle
C. cross-site scripting
D. insecure API
Correct Answer: B
NEW QUESTION 11:
What is the benefit of performing device compliance?
A. Verification of the latest OS patches
B. Device classification and authorization
C. Providing multi-factor authentication
D. Providing attribute-driven policies
Correct Answer: A
NEW QUESTION 12:
While using Cisco Firepower\’s Security Intelligence policies, which two criteria is blocking based upon? (Choose two.)
A. port numbers
B. URLS
C. IP addresses
D. protocol IDs
E. MAC addresses
Correct Answer: BC
NEW QUESTION 13:
Where are individual sites specified to be blacklisted in Cisco Umbrella?
A. application settings
B. content categories
C. security settings
D. destination lists
Correct Answer: D
Reference: https://docs.umbrella.com/deployment-umbrella/docs/working-with-destination-lists
…
[Free Download]CCIE Security/CCNP Security 350-701 SCOR exam material:
https://drive.google.com/file/d/1nrGX0OHNPH6_sX2MlYWI8i4jCVVOUV7g/view?usp=sharing
The above are free to share 15 350-701 SCOR exam material, check this link to get more exam questions and answers.